TBA
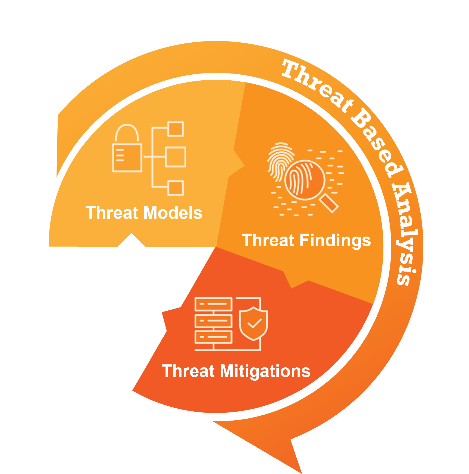
Threat-Based Analysis
The three segments of threat-based analysis—threat models, threat findings, and threat mitigations—are applied to systems to provide time-efficient results and enable immediately actionable controls.
Initial threat priorities are developed based on confidentiality, integrity, and availability (CIA), a common cybersecurity model that ranks C, I, and A in priority order, where each is defined as:
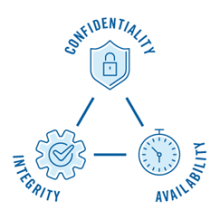
- Confidentiality – reserving authorized restrictions on information access and disclosure, including means for protecting personal privacy and proprietary information;
- Integrity – guarding against improper information modification or destruction and maintaining information non-repudiation and authenticity; and
- Availability – maintaining timely and reliable access to and use of information.
Outcomes

- The Shamrock Cyber Threat Model combines defined user roles, CIA priorities, and system and context diagrams.
- The Shamrock Cyber Threat Findings are determined based on analyzed data from the threat model.
- The Shamrock Cyber Threat Profile triages and prioritizes actionable mitigations.