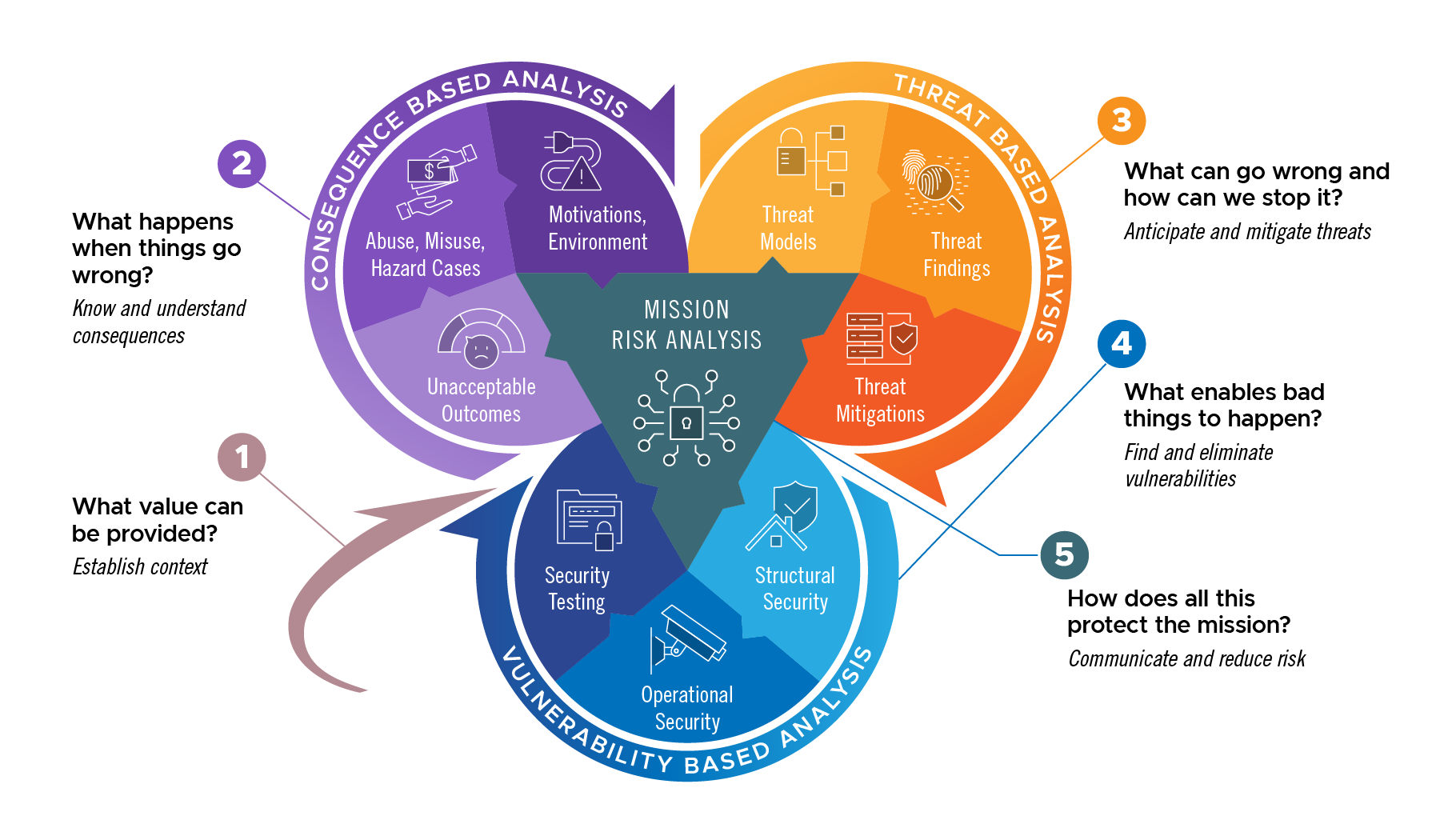
Shamrock Cyber
By combining the analysis of consequences, threats, and vulnerabilities, Shamrock Cyber significantly reduces the effort to prioritize, communicate, and mitigate risks throughout the development lifecycle of software and other types of systems
Shamrock Cyber
(Image by Hannah Kauffman | Pacific Northwest National Laboratory)