Cybersecurity
Maturity
Models
Cybersecurity
Maturity
Models
A maturity model provides a set of indicators that represent capability and progression in a particular discipline. A maturity model provides a benchmark against which an organization can evaluate its current level of performance and, if warranted, set programmatic goals and priorities for improvement. The underlying principle is that not all organizations need to have the same maturity in a given discipline. Organizations facing high risks and with available resources typically require a more mature program than organizations that are facing low risk or are just starting to develop their capability.
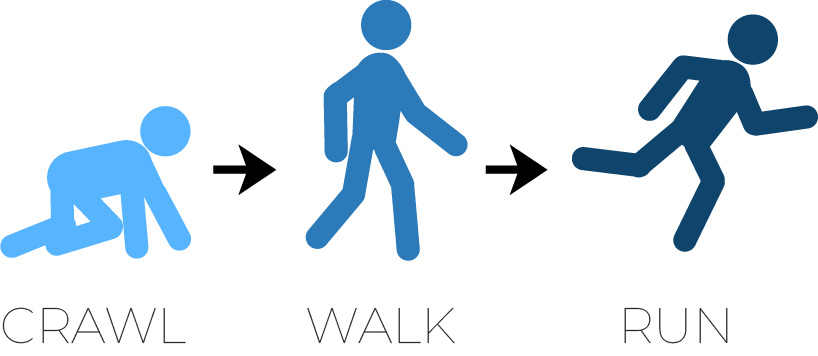
The human mobility analogy in a maturity model is the process of first learning to crawl, then walk, and then run. Young children don’t jump from crawlers to runners overnight, they need to develop their muscles and coordination over time and with practice to achieve their mobility goals. Similarly, organizations need to first develop a core capability that provides some level of performance before they work to grow their capabilities in a thoughtful, systematic manner.
PNNL scientists and researchers have developed a robust portfolio of maturity models that are free and available for many organizations to use. Our core models focus on cybersecurity applications, but some focus on other programmatic issues, such as energy infrastructure resilience, chemical facility security, supply chain security and the secure design and development of software. Though the primary audience for these tools is the energy sector many of these tools are applicable to multiple sectors.
For example, a cybersecurity maturity model assesses the maturity of an organization’s cybersecurity program and identifies areas that could be improved to address the continually evolving cyber threat environment. This type of model helps organizations improve their cybersecurity posture, develop a roadmap that prioritizes improvements, and helps subject matter experts communicate effectively with senior management to obtain support for risk-based cybersecurity improvements.
Maturity models can used regardless of size, type, or industry of the organizations. The models can focus on a broad area of interest (e.g., cybersecurity or resilience capabilities) across an entire organization, they can examine programmatic capabilities at a single facility, or they focus on a component of process operations.
Maturity models in PNNL’s portfolio are based on the Cybersecurity Capability Maturity Model (C2M2) framework. The C2M2 framework was developed through a public-private partnership effort sponsored by the U.S. Department of Energy. Work on the C2M2 began in 2012 and was conducted to improve electricity subsector cybersecurity capabilities and to better understand the cybersecurity posture of the electric power grid. Today the C2M2 and other PNNL maturity models are available for online access on the model’s webpage. The on-line versions of the models are provided as HTML-based software tools. The tools are designed to be easy to use and provide security and privacy for users. Extensive training materials are provided on each model’s “Resources” webpages and typically includes a general model user guide, guidance on how to organize and facilitate a self-assessment, and a step-by-step instruction manual for the tools.
Security and privacy are important features of our online tools and were a “must have” specified by our industry partners. All data entered by the user and all model output reports are generated and stored on the user’s computer. No user data are ever communicated to the model server. If a user requests an off-line version of our tools, our team will provide that product.
The models are used by thousands of people across a diverse range of countries around the globe. We can use website traffic analysis tools to determine the frequency with which our tools and support products are accessed and other generic information, but no information can be acquired about specific users and the information they enter into the tools.
We invite organizations to access and make use of our maturity models (summarized below) to assess their programmatic maturity in a variety of areas. We value user feedback on the models. You can share your feedback and comments with the PNNL cybersecurity team.
Featured Maturity Models
 |
VIEW SITE |
The Cybersecurity Capability Maturity Model (C2M2) was developed to assess the maturity of a energy sector organization’s cybersecurity program (it is also used by other critical infrastructure sector). The model can be used to identify areas where cost-effective enhancements can quickly improve cybersecurity programs. The current version of the C2M2 (Version 2.1) was released in June 2022 and uses 356 practices to evaluate performance across 12domains. Development work on the C2M2 began in 2012 and its original version and all subsequent major revisions have involved cooperative efforts by energy industry experts from a diverse group of public agencies, private institutes, and industry. C2M2 work is sponsored by the U.S. Department of Energy’s Office of Cybersecurity, Energy Security, and Emergency Response (CESER). The C2M2 website and tools are freely available in North America and around the world.
 |
VIEW SITE |
The Cybersecurity Capability Maturity Model-Nuclear (C2M2-Nuclear) was developed to assess the maturity of a nuclear sector organization’s cybersecurity program. This includes nuclear power plants, research reactors, nuclear fuel fabrication, nuclear waste processing and disposal, nuclear medicine facilities, and others. C2M2-Nuclear is based on C2M2 Version 2.1 and uses 413 practices to evaluate performance across 12 domains. The development and operation of C2M2-Nuclear is sponsored by the U.S. Department of Energy’s Office of International Nuclear Security (INS). The C2M2-Nuclear is freely available to registered users. A registration request can be submitted using the Register page on the C2M2-Nuclear webpage.
 |
VIEW SITE |
The Transmission Resiliency Maturity Model (TRMM) is a tool for electricity transmission organizations to objectively evaluate and benchmark their current transmission resiliency policies, programs, and investments. The objective is to assist the transmission organization to target and prioritize improvements and enhance the overall resilience of the power grid. This U.S. Department of Energy-sponsored model was developed through a public-private partnership that included PNNL, Electric Power Research Institution, the North American Transmission Forum, and more than a dozen transmission utilities.
 |
VIEW SITE |
The Facility Cybersecurity Framework (FCF) suite of maturity models provides tools to assess the cybersecurity maturity of facilities using an array of standards and guidance. It includes, but is not limited to the following tools::
- The FCF uses the National Institute of Standards and Technology (NIST) cybersecurity framework to help building and facility owners and operators assess and manage cybersecurity risks.
- The FCF-Risk Management Framework (RMF) Hybrid can perform a standard Management Framework (RMF_ assessment and generate both FCF and RMF compliance/maturity scores.
- The F-C2M2 is an alternate presentation of the C2M2. It allow organizations to assess their building or facility’s cybersecurity maturity using the C2M2 framework from within the FCF suite.
- The FCF-Primer enables the user to conduct a quick review of their facility’s security posture before committing resources to a full FCF assessment. The FCF-Primer can be used prior to an FCF assessment or to track enhancements during the post-assessment/gap-mitigation activities.
The FCF includes an array of other tools including the:
- Qualitative Risk Assessment (QRA) tool to assist facility owners and operators in performing risk-based asset management.
- The FCF Cybersecurity Training Game provides dynamic, game-based cybersecurity training
- The Mitigation of Externally Exposed Energy Delivery Systems (MEEDS) helps users securely identify potentially vulnerable devices that are inadvertently exposed to the public internet.
Models Undergoing Development or Testing
 |
VISIT SITE |
The Secure Design and Development C2M2 (SD2-C2M2) is a tool that can be used by hardware, software, and system developers and integrators to assess their design and development practices and procedures against a set of best-practice concepts to determine the maturity level of their processes. The tool can then compare the maturity levels against a set of management derived levels to determine where improvements can be made. A new version of the SD2-C2M2 and a full suite of guides are being developed and password to access the SD2-C2M2 tool can be requested by through the SD2-C2M2 registration webpage.
 |
VIEW SITE |
The Chemical Security Assessment Model (CSAM) assists chemical facilities and laboratories in identifying the maturity of the chemical security program and to identify programmatic areas to strengthen to maintain a desired level of security. A prototype of the model was released in late 2022 and further enhancements are planned in late 2023. CSAM shares a website with the CLiCS model.
 |
VIEW SITE |
The Chemical Lifecycle and Supply Chain Security (CLiCS) Model assists organization in identifying the maturity of the chemical security program used to address the lifecycle security risks associated with hazardous and weaponization chemicals. This model follows these chemicals of interest from their precursors, through management, storage, transportation, sale to customers, use, and eventual disposal. CLiCS shares a website with the CSAM Tool.
 |
|
The Supply Chain Security Maturity Model (SCSMM) is currently under development. It will assess the maturity of an organization or facility’s supply chain security program. It allows users to assess their programmatic performance in nine different domains important to supply chain security, including Supply Chain Threat, Vulnerability and Risk Management; Supplier Management; Procurement; Asset Delivery and Installation; Asset and Change Management; and Workforce Management.
Training Tools
The FCF Cybersecurity Training Game is designed for a spectrum of facility owners and operators. It provides dynamic, game-based cybersecurity training. Users pick a scenario and are then confronted with a series of real-world cyberattacks on their facility. Cybersecurity resources to thwart the attack are constrained to mimic real-world limitations. Attacks may impact both information and operational technology systems.
Contact
Those interested in learning more are encouraged to email our Maturity Modeling team at MaturityModels@pnnl.gov for the quickest response.